The Personnel Security page details the NCUA personnel security vetting process, applicable forms and links, investigative requirements, and reporting requirements for applicants, employees, contractors, and interns. The page also details pertinent statements to include Privacy Act and Use of Fingerprints.
Vetting Process Overview
The National Credit Union Administration (NCUA) Personnel Security and Suitability Program (PERSEC) manages the responsibilities and procedural requirements for investigations, suitability adjudications, fitness determinations, and security clearance determinations for employees, applicants, appointees, contractors, and affiliates. PERSEC vets all personnel prior to granting access to facilities, systems, or non-public information, and through continuous vetting.
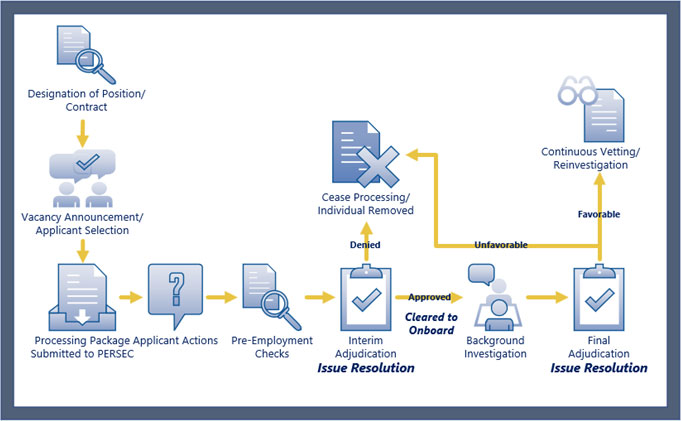
The Personnel Security Vetting Process begins with the risk and sensitivity designation of the position description or the contract statement of work. This process is meant to standardize the process of assessing the needed level of investigation across the government. Once completed, the office can post a vacancy announcement and select a candidate for the position or contract. After an individual has been tentatively hired or selected for a contract position, the processing package with applicable vetting forms is sent to the Personnel Security Office or PERSEC. PERSEC will notify the applicant, employee or contractor, of the next steps in the process. The applicant actions include fingerprint enrollment and security questionnaire completion via the NBIS system.
After both actions are completed, the process moves into the interim adjudication and issue resolution phase. An NCUA adjudicator will review all of the submitted information as well as the results from the pre-employment checks (i.e., credit history check, criminal history check, work authorization, etc.) to determine whether or not the employee applicant or contractor is suitable or fit to work for or on behalf of the NCUA. If issues are identified, the adjudicator will reach out to the applicant to address concerns. The individual can then submit additional information in writing to be considered by the adjudicator.
If a favorable determination is rendered, notification will be sent to the submitting office that the person is cleared to onboard. The background investigation is scheduled, if needed, through our investigations service provider, the Defense Counterintelligence and Security Agency. Once the investigation is complete, the NCUA adjudicators will review the investigation and render a final determination. If issues are identified, issue resolution can occur at this time as well. If a favorable determination is rendered, the individual is placed into Continuous Vetting with a reinvestigation requirement.
If an unfavorable determination is rendered, either at the interim or final adjudication phase, the individual cannot work for or on behalf of the NCUA and must be removed. If the individual was granted a favorable interim, the individual will be removed.
Interim Vetting Process
Applicants and Contractor Personnel will be asked to complete the necessary paperwork to start the personnel vetting process. To allow entry on duty, PERSEC must render a preliminary or interim determination of trust after the receipt and favorable review of the completed paperwork and security questionnaire, fingerprint check results, and other pre-hire checks. The steps in the process are dependent on the position or contract the individual will occupy.
If derogatory information is identified, as defined under the applicable guidelines, correspondence will be sent to the individual by NCUA PERSEC via email, affording the individual an opportunity to address the concern(s). NCUA PERSEC will consider all available information prior to making an interim determination.
Background Investigation Requirement
Anyone seeking employment at NCUA will undergo a background investigation, with the level dependent upon position or contract. The full background investigation will be processed by our investigations service provider, the Defense Counterintelligence and Security Agency (DCSA), and the scope of the investigation will vary depending on the nature of the position or contract the applicant or contractor personnel will occupy at the NCUA, and the access requirements to facilities, systems, or information. When a background investigation is required, PERSEC will provide the link to DCSA’s eApp system to complete the appropriate investigative forms to process the background investigation. Access to the eApp system is by invitation only. For more information on the DCSA background investigation process, visit Investigations & Clearance Process (dcsa.mil).
Helpful Hints
- Check emails regularly and pay attention to the deadlines provided.
- Be honest throughout the entire process. Lying about your conduct may be worse than the conduct itself.
- If you are contacted regarding derogatory information, this is YOUR opportunity to provide PERSEC with additional information PRIOR TO an interim or final adjudicative determination being made.
Final Adjudication Phase
Once the background investigation is completed, the gathered information is evaluated by trained adjudicators who assess the individual’s background against predetermined standards set by federal regulations (e.g., Adjudicative Guidelines). NCUA will render a suitability or fitness determination prior to allowing individuals to work as a federal employee or contractor of the NCUA. If the applied position is a sensitive national security position or will require eligibility for access to classified national security information (i.e., a clearance), NCUA will also adjudicate the background investigation under those standards.
Similar to the interim process, if NCUA identifies derogatory information related to the personnel vetting standards, NCUA will provide an opportunity to respond via written correspondence. NCUA employs the holistic "whole person" concept during the adjudication of all background investigations. This entails the consideration of every piece of information concerning one’s personal and professional background in making adjudicative determinations while balancing the need to protect and promote the efficiency of the federal service.
FAQs
Self-Reporting Requirements
Personnel Security
Employees and contractors are required to promptly self-report to OCSM any circumstances that may affect their suitability, fitness, or national security determination. Items self-reported within 14 calendar days will normally be viewed as promptly reported. Self-reporting, while mandatory, is also a question of personal integrity and is certainly preferable to the incident or charge being discovered through other means.
Listed below are incidents and life events where self-reporting is required; however, this list is not all encompassing. If you are unsure of whether to report or not, please reach out to the Personnel Security office at PersonnelSecurity@NCUA.gov.
Sample Reportable Activities
- Reporting any change or known alteration in legal name (i.e., due to marriage, divorce, etc.) date of birth, place of birth, or social security number;
- Arrests, regardless of whether charges were filed or whether charges were dismissed;
- Illegal drug activity (see note below);
- Alcohol or drug related treatment;
- Financial problems, to include bankruptcy, garnishments, judgments, delinquency of over 120 days of any debt, liens, or evictions;
- Attempted elicitation, exploitation, blackmail, coercion, or enticement to obtain classified information or other proprietary information specifically prohibited by law from disclosure regardless of means;
- Unauthorized access to information, information systems, or classified information; and
- Unauthorized disclosure or improper handling or storage of classified information.
Note: In accordance with E.O. 12564, Drug-Free Federal Workplace, the term illegal drug means a controlled substance included in Schedule I or II, as defined by section 802(6) of Title 21 of the United States Code, the possession of which is unlawful of under chapter 13 of that Title. Marijuana and THC remain Schedule I controlled substances under the CSA (see items (d)(23) and (31)).
Insider Threat
What is an Insider Threat?
An insider threat is the potential risk a person who has, or once had, authorized access to NCUA resources (to include facilities, information, equipment, networks, and/or systems) misuses that access to negatively impact the agency. This misuse of access may either be intentional (e.g., conducted with malicious intent) or unintentional (e.g., conducted through negligence). Outcomes of insider threat incidents may include, among other things: compromise of critical assets, physical violence, loss of revenue or intellectual property, fraud, compromise of sensitive data, and/or organizational risk to reputation.
Helpful Hints
An insider’s misuse of access does not have to be intentional to cause damage. Unintentional insiders who lack awareness or do not practice strong cyber hygiene risk harming the agency or even advancing our adversaries’ objectives unknowingly.
Recognizing Indicators
Individuals at risk of becoming insider threats, and those who ultimately cause significant harm, often exhibit warning signs, or indicators. Potential Risk Indicators include a wide range of individual predispositions, stressors, choices, actions, and behaviors. Personal stressors arise from situations that cause strain or tension in an individual’s personal or professional life. Though unexpected events can occur to anyone at any time, stressors can act as triggers to individuals with the potential to become an insider threat. Not all of these indicators will be evident in every insider threat and not everyone who exhibits these behaviors is doing something wrong. Early reporting allows the NCUA Insider Threat Program to pursue a multi-disciplinary approach to deterring threats and potential issues early on, before a problem occurs. For additional information on behavioral risk indicators, visit CDSE Indicators Job Aid.
How to Report Concerns
To protect against insider threats, the NCUA maintains a proactive and prevention-focused insider threat mitigation program. An effective program can protect critical assets, deter violence, counter unintentional incidents, prevent loss of revenue or intellectual property, avert sensitive data compromise, and prevent organizational reputation ruin, among many other potential harmful outcomes. The most important resource the NCUA has to counter insider threats are the insiders themselves. All NCUA personnel have a responsibility to protect the agency and to report activities that could pose risk to the NCUA mission, its information, resources (including personnel), or capabilities.
If you notice someone exhibiting any of the indicators listed above or whom you feel poses a risk to the NCUA, themselves, or others, please report to your immediate supervisor or directly to the OCSM by contacting the Insider Threat Program Manager or OCSM Leadership at InsiderThreat@NCUA.gov.
Privacy Act Statement
FBI Privacy Act and Use of Fingerprints Statement
Use of Fingerprints
As a NCUA employee, appointee with a conditional offer, contractor, student, or other person requesting access to NCUA facilities or information who is the subject of a national fingerprint- based criminal history records check, you have certain rights with respect to the collection and use of your fingerprints and to the accuracy of the information obtained from the check.
You are hereby advised that your fingerprints will be used to check the Criminal History Record Information (CHRI) of the Federal Bureau of Investigation (FBI). You are being provided with the Privacy Act Statement, see below, prior to the submission of your fingerprints and associated personal information to the FBI or enrollment in a continuous evaluation/vetting program. Your fingerprints will be maintained, and future instances of criminal activity will result in notification to the NCUA. Enrollment will terminate upon your affiliation with the NCUA ending.
NCUA officials making a determination of your fitness or suitability for employment and/or a national security decision will not take adverse action against you, based in whole or in part upon the CHRI, without first providing you an opportunity to challenge the information. You may submit a challenge request directly to the FBI at https://www.edo.cjis.gov or in writing: FBI CJIS Division, Attention: Criminal History Analysis Team 1, 1000 Custer Hollow Road, Clarksburg, WV 26306.
You will further be afforded a reasonable amount of time to address or complete the record (or decline to do so) before the officials deny fitness or suitability, or national security eligibility based on information in the criminal history record. This delay may affect the ability for the NCUA to make a determination regarding your eligibility and therefore your ability to commence work may be delayed.
Fingerprint Privacy Act Notice
AUTHORITY: 12. U.S.C. 1751, et. seq., Executive Orders 10577, 10865, 12333, 12968, 13467, 13488, 13764; 5 U.S.C. §§ 3301, 3302, 7301, and 9101. The FBI’s acquisition, preservation, and exchange of fingerprints and associated information is generally authorized under 28 U.S.C. 534. Depending on the nature of your application, supplemental authorities include Federal statutes, State statutes pursuant to Public Law 92-544, Presidential Executive Orders, and federal regulations. Providing your fingerprints and associated information is voluntary; however, failure to do so may affect completion or approval of your application.
PURPOSE: Your fingerprints and associated information/biometrics will be used as part of NCUA’s suitability and national security clearance program, including pre-employment screening, and the initiation of background investigations, suitability and security adjudications, and determinations regarding logical and physical access to federally controlled facilities and information systems.
Certain determinations, such as employment, licensing, and security clearances, may be predicated on fingerprint-based background checks. Your fingerprints and associated information/biometrics may be provided to the FBI for the purpose of comparing your fingerprints to other fingerprints in the FBI’s Next Generation Identification (NGI) system or its successor systems (including civil, criminal, and latent fingerprint repositories) or other available records of the employing, investigating, or otherwise responsible agency. The FBI may retain your fingerprints and associated information/biometrics in NGI after the completion of this application and, while retained, your fingerprints may continue to be compared against other fingerprints submitted to or retained by NGI.
ROUTINE USE(S): The information you provide may be shared with parties outside NCUA as necessary to document the outcome of adjudicative determinations for suitability, fitness, and/or national security clearances. Your contact information is used for communication and authentication purposes. The information may be shared with designated officers and employees of agencies, offices, and establishments in the executive branch of the Federal Government when the NCUA conducts an investigation of an individual for purposes of granting a security clearance, or for the purpose of making a determination of qualifications, suitability, or loyalty to the U.S. Government, or access to classified information or restricted areas. Other routine uses include, but are not limited to, disclosures to: employing, governmental, or authorized nongovernmental agencies responsible for employment, contracting, licensing, security clearances, and other suitability determinations; local, state, tribal, or federal law enforcement agencies; criminal justice agencies; and agencies responsible for national security or public safety.
Also, during the processing of this application and for as long thereafter as your fingerprints and associated information/biometrics are retained in NGI, your information may be disclosed pursuant to your consent, and may be disclosed without your consent as permitted by the Privacy Act of 1974 and all applicable Routine Uses as may be published at any time in the Federal Register, including the FBI’s Blanket Routine Uses. Routine uses include, but are not limited to, disclosures to: employing, governmental, or authorized nongovernmental agencies responsible for employment, contracting, licensing, security clearances, and other suitability determinations; local, state, tribal, or federal law enforcement agencies; criminal justice agencies; and agencies responsible for national security or public safety.
EFFECTS OF NOT PROVIDING INFORMATION: Failure to provide this information may result in the NCUA being unable to complete its suitability and/or clearance processes to render a final decision regarding your suitability for initial or continued employment.
SORNS: NCUA-1, Personnel Access & Security System (PASS), 84 FR 12748, OPM CENTRAL-9, Personnel Investigations Records, 81 FR 70191, and FBI-009, The Next Generation Identification (NGI) System, 84 FR 54182.
Forms
Links
- USAccess Find a Credentialling Center
- USAccess Required Identification Documents
- Background Investigations Process for Applicants
- eApp Applicant Access
- Help Filling Out the eApp Forms
- Verify Your DCSA Investigator
- Access Your DCSA Records
Contact Information
For questions regarding the NCUA Personnel and Security Program, please email PersonnelSecurity@NCUA.gov.


